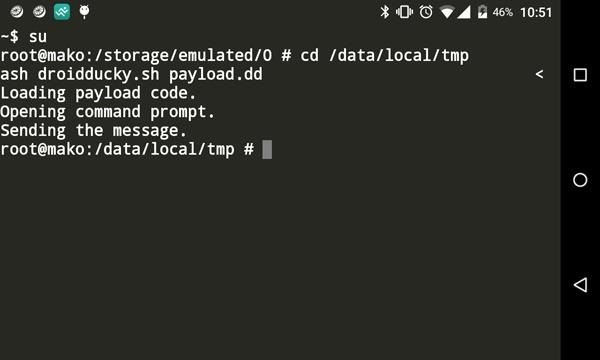
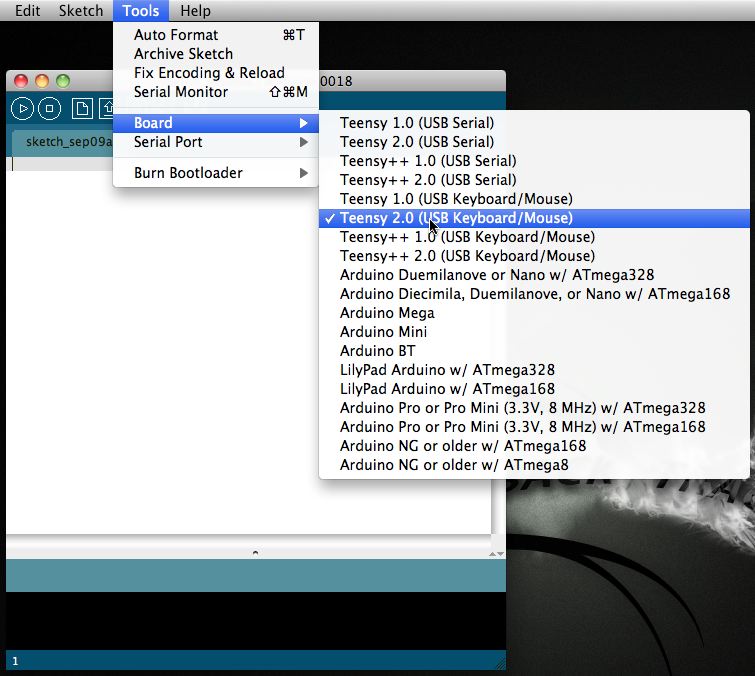
PDF) Spyduino: Arduino as a HID exploiting the BadUSB vulnerability | Vagelis Karystinos - Academia.edu
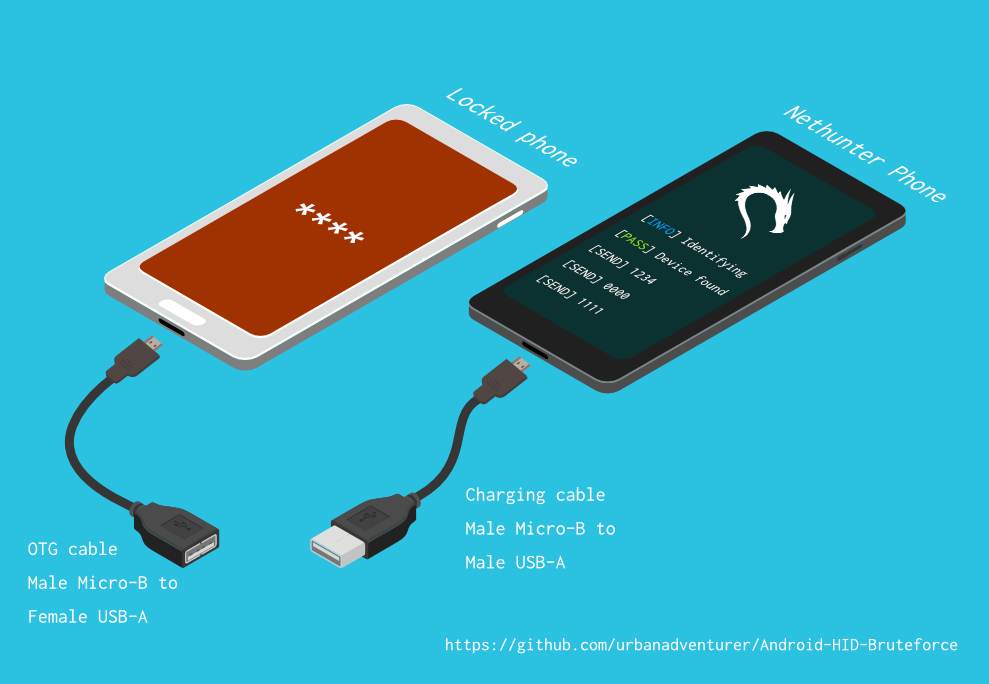
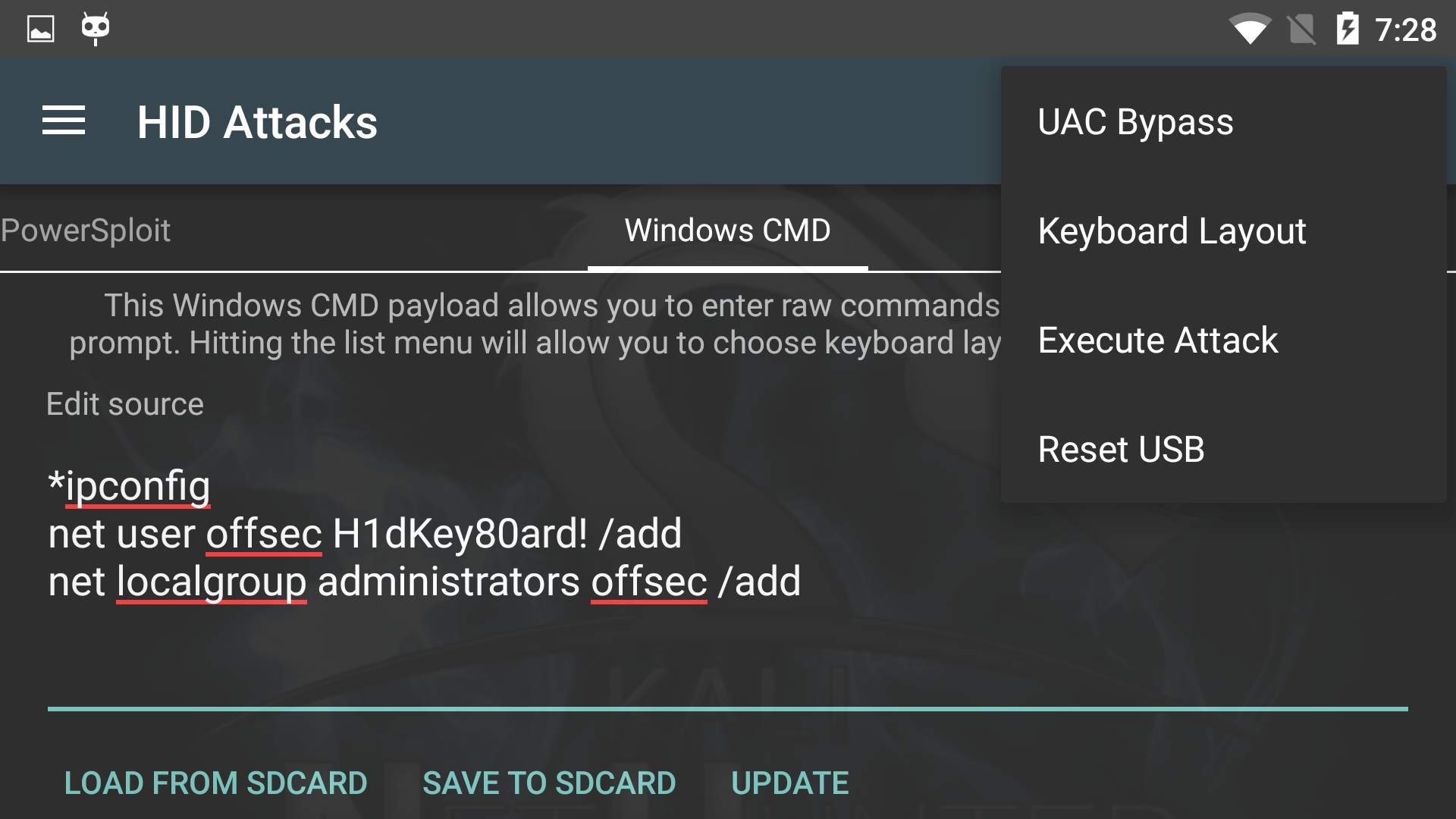
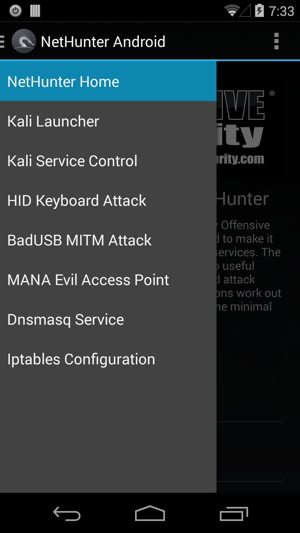
USB HID Attacks. USB HID devices are the way we interact… | by evildaemond | Heck the Packet | Medium

Overview | The Foul Fowl -- Keystroke Injection Attack Tool with Gemma M0 | Adafruit Learning System